· Tim van der Weijde · DevOps · 3 min read
Secure Remote Powershell

What can you do with it?
With Remote PowerShell, you can execute commands on a computer using a temporary or persistent connection. As a result, you can use the complete PowerShell framework and the modules installed on the remote computer.
Remote PowerShell can be used for all kinds of reasons. For instance, I’m using a remote PowerShell script in a CI/CD setup (wiki). During deployment, a new secure website is created, and certificates for TLS are installed.
Why Secure?
Without a secure connection, all information is visible during transport to the remote machine, leaving it susceptible to a man-in-the-middle attack.
It takes a bit more effort to make the connection secure, but that’s no reason to skip it. If you have any problems setting up secure remote PowerShell, please leave a comment. I’m happy to help you get it right.
Self-signed Certificate
To create a secure connection, we need a certificate. For this solution, I’m creating a Self-signed Certificate (wiki). This certificate is used on the remote machine and won’t be visible to any client.
We’re going to use PowerShell with the New-SelfSignedCertificate cmdlet. This cmdlet is part of the Public Key Infrastructure module (PKI):
# Create Self-signed certificate
$Cert = New-SelfSignedCertificate -DnsName doctorwho.bluecape.nl -CertStoreLocation cert:\LocalMachine\My
Download the full script at the end of the blog post.
Execute the above script on the remote machine. After that, you should see the certificate installed on the machine. (Open the Certificate Manager Tool with “certmgr”)
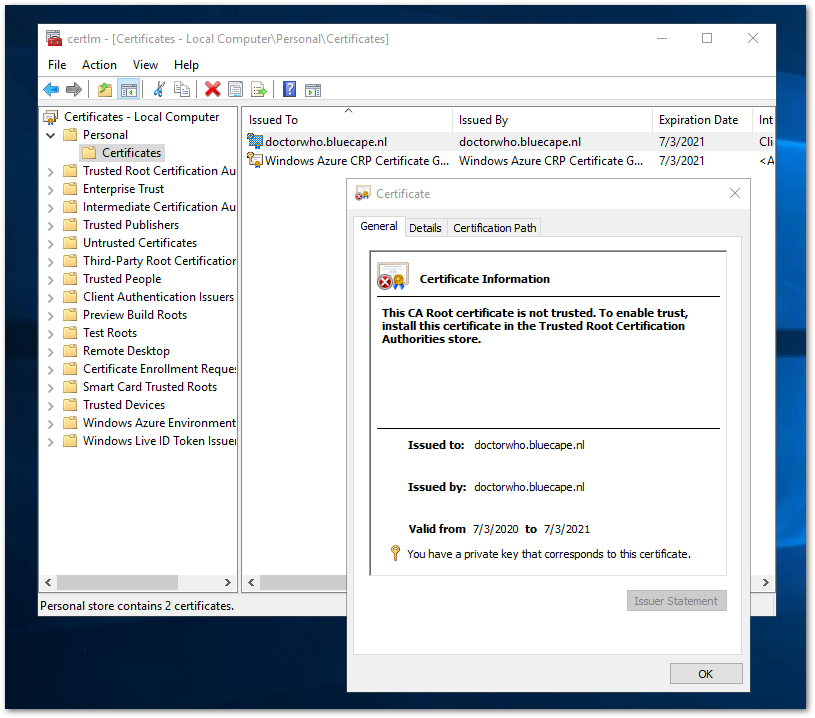
This self-signed certificate is generated with the following default settings:
- Cryptographic algorithm: RSA
- Key length: 2048 bit
- Acceptable key usage: Client Authentication and Server Authentication
- The certificate can be used for: Digital Signature, Key Encipherment
- Validity period: 1 year
It’s important to know that Remote PowerShell requires Server Authentication in the certificate.
Web Services for Management (WSMAN)
Remote PowerShell uses the WSMAN web services to create a secure connection. The following code will enable an HTTPS listener for WSMAN, using the thumbprint of the generated self-signed certificate:
New-Item -Path WSMan:\LocalHost\Listener -Transport HTTPS -Address * -CertificateThumbPrint $Cert.Thumbprint -Force
Download the full script at the end of the blog post.
The new listener will accept all IP addresses (see asterisk *). Of course, you can make this more specific to your needs.
Enabling Remote PowerShell
Enabling Remote PowerShell is simple. Just execute the following command to enable it on the remote machine:
Enable-PSRemoting
Download the full script at the end of the blog post.
Run this command only once on each machine that will receive commands. In other words, you do not have to run it on machines that only send commands.
Firewalls & Ports
A final step to enable Remote PowerShell is to add a firewall rule for the default port 5986:
New-NetFirewallRule -DisplayName 'WinRM Remote Powershell HTTPS-In' -Name 'WinRM Remote Powershell HTTPS-In' -Profile Any -LocalPort 5986 -Protocol TCP
Download the full script at the end of the blog post.
The Result
That’s it. The machine is ready to receive a remote connection. Try it out on your client machine.
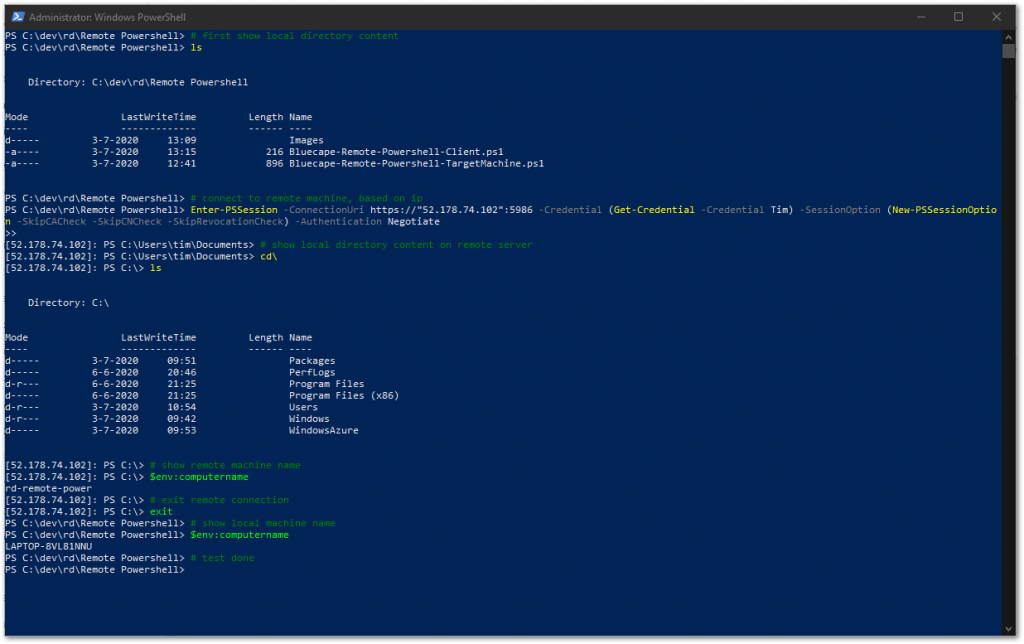
It’s now possible to execute all kinds of commands on the remote machine!
Please leave a comment below if you like this or have any questions. Thank you!
 Bluecape
Bluecape